上次分享了集中式VXLAN IP网关实验,该方案进行二层VXLAN业务终结的同时,还对内层封装的IP报文进行三层转发处理。虽然节省了设备资源,但不同VXLAN之间的流量以及VXLAN访问外界网络的流量全部由集中式VXLAN IP网关处理,网关压力较大,并加剧了网络带宽资源的消耗。在在分布式VXLAN IP网关方案中,每台VTEP设备都可以作为VXLAN IP网关,对本地站点的流量进行三层转发,很好地缓解了网关的压力。这次就来学习分布式VXLAN网关如何部署。
分布式VXLAN IP网关组网中,可分为三类访问过程:
- 相同VXLAN内不同站点的虚拟机通信
- 不同VXLAN间不同站点的虚拟机通信
- 虚拟机与外部网络的三层通信

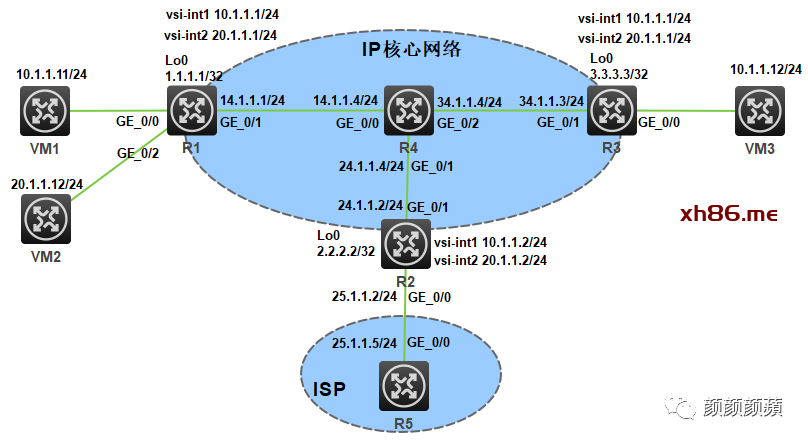
R1、R3为分布式VXLAN IP网关设备,R2为与广域网连接的边界网关设备,R5为广域网内的三层设备。虚拟机VM 1和VMA3属于VXLAN 10,VM 2属于VXLAN 20。通过分布式VXLAN IP网关实现不同VXLAN网络的三层互联,并通过边界网关实现与广域网的三层互联。
具体需求为:
- 不同VTEP之间手工建立VXLAN隧道。
- 手工关联VXLAN和VXLAN隧道。
- 站点之间的泛洪流量采用头端复制的方式转发。
- VM 1、VM 2、VM 3之间可以互访,且VM 1、VM 2和VM 3都可以访问外部网络。
组网图
配置步骤
(1) 配置IP地址和单播路由协议
# 在VM 1、VM 2和VM 3上分别指定网关地址为10.1.1.1、20.1.1.1、10.1.1.1,具体配置过程略。
# 配置各接口的IP地址和子网掩码;在IP核心网络内配置OSPF协议,确保路由器之间路由可达;配置R2和R5为 25.1.1.0/24网段地址,R5上配置静态路由,具体配置如下:
R1
interface LoopBack0ip address 1.1.1.1 255.255.255.255interface GigabitEthernet0/1ip address 14.1.1.1 255.255.255.0ospf 1 router-id 1.1.1.1area 0.0.0.0network 1.1.1.1 0.0.0.0network 14.1.1.0 0.0.0.255
R2
interface LoopBack0ip address 2.2.2.2 255.255.255.255interface GigabitEthernet0/1ip address 24.1.1.2 255.255.255.0interface GigabitEthernet0/0ip address 25.1.1.2 255.255.255.0ospf 1 router-id 2.2.2.2area 0.0.0.0network 2.2.2.2 0.0.0.0network 24.1.1.0 0.0.0.255
R3
interface LoopBack0ip address 3.3.3.3 255.255.255.255interface GigabitEthernet0/1ip address 34.1.1.3 255.255.255.0ospf 1 router-id 3.3.3.3area 0.0.0.0network 3.3.3.3 0.0.0.0network 34.1.1.0 0.0.0.255
R4
interface LoopBack0ip address 4.4.4.4 255.255.255.255interface GigabitEthernet0/0ip address 14.1.1.4 255.255.255.0interface GigabitEthernet0/1ip address 24.1.1.4 255.255.255.0interface GigabitEthernet0/2ip address 34.1.1.4 255.255.255.0ospf 1 router-id 4.4.4.4area 0.0.0.0network 4.4.4.4 0.0.0.0network 14.1.1.0 0.0.0.255network 24.1.1.0 0.0.0.255network 34.1.1.0 0.0.0.255
R5
interface GigabitEthernet0/0ip address 25.1.1.5 255.255.255.0ip route-static 10.1.1.0 24 25.1.1.2ip route-static 20.1.1.0 24 25.1.1.2
2.配置VXLAN
R1
# 开启L2VPN能力
l2vpn enable # 在R1和R2之间建立VXLAN隧道:
创建模式为VXLAN的隧道接口Tunnel12
指定隧道的源端地址为本地接口Loopback0的地址1.1.1.1
指定隧道的目的端地址为Router B上接口Loopback0的地址2.2.2.2
R1和R3建立VXLAN隧道类似:
interface Tunnel12 mode vxlansource 1.1.1.1destination 2.2.2.2interface Tunnel13 mode vxlansource 1.1.1.1destination 3.3.3.3
# 创建VSI实例vpna和VXLAN 10,并将Tunnel1和Tunnel2与VXLAN 10关联
vsi vpnavxlan 10tunnel 12tunnel 13vsi vpnbvxlan 20tunnel 12tunnel 13
#在接入服务器的接口G0/0上关联VSI实例vpna,G0/2上关联VSI实例vpnb
interface GigabitEthernet0/0xconnect vsi vpnainterface GigabitEthernet0/2xconnect vsi vpnb
# 创建VSI虚接口VSI-int1,并为其配置IP地址和MAC地址,该IP地址作为VXLAN 10内虚拟机的网关地址,指定该VSI虚接口为分布式本地网关接口,并开启本地代理ARP功能。
interface vsi-interface 1ip address 10.1.1.1 255.255.255.0mac-address 1-1-1distributed-gateway locallocal-proxy-arp enable
# 创建VSI虚接口VSI-int2,并为其配置IP地址和MAC地址,该IP地址作为VXLAN 20内虚拟机的网关地址,指定该VSI虚接口为分布式本地网关接口,并开启本地代理ARP功能。
interface vsi-interface 2ip address 20.1.1.1 255.255.255.0mac-address 2-2-2distributed-gateway locallocal-proxy-arp enable
# 开启分布式网关的动态ARP表项同步功能,默认关闭。
arp distributed-gateway dynamic-entry synchronize# 配置VXLAN 10所在的VSI实例和接口VSI-int1关联。
vsi vpnagateway vsi-interface 1
# 配置VXLAN 20所在的VSI实例和接口VSI-int2关联。
vsi vpnbgateway vsi-interface 2
# 配置策略路由,指定IPv4报文如果未找到匹配的路由表项,则设置报文的下一跳为Router B上接口VSI-int1的IP地址10.1.1.2。
acl advanced 3000rule 0 permit ippolicy-based-route vxlan10 permit node 5if-match acl 3000apply default-next-hop 10.1.1.2
# 配置策略路由,指定IPv4报文如果未找到匹配的路由表项,则设置报文的下一跳为Router B上接口VSI-int2的IP地址20.1.1.2。
policy-based-route vxlan20 permit node 5if-match acl 3000apply default-next-hop 20.1.1.2
# 在VSI虚接口VSI-interface1和VSI-int2上应用策略路由。
interface vsi-interface 1ip policy-based-route vxlan10interface vsi-interface 2ip policy-based-route vxlan20
其余VTEP设备与R1配置步骤相同,配置如下:
R2
l2vpn enableinterface Tunnel31 mode vxlansource 3.3.3.3destination 1.1.1.1interface Tunnel32 mode vxlansource 3.3.3.3destination 2.2.2.2vsi vpnagateway vsi-interface 1vxlan 10tunnel 31tunnel 32vsi vpnbgateway vsi-interface 2vxlan 20tunnel 31tunnel 32interface GigabitEthernet0/0xconnect vsi vpnainterface vsi-interface 1ip address 10.1.1.1 255.255.255.01-1-1localenableinterface vsi-interface 2ip address 20.1.1.1 255.255.255.02-2-2localenablearp distributed-gateway dynamic-entry synchronizeacl advanced 3000rule 0 permit ipvxlan10 permit node 5if-match acl 3000apply default-next-hop 10.1.1.2interface vsi-interface 1ip policy-based-route vxlan10

(1)验证分布式VXLAN IP网关设备R1
# 查看R1上的Tunnel接口信息,可以看到VXLAN模式的Tunnel接口处于up状态。
interface Tunnel 12Tunnel12Current state: UPLine protocol state: UPDescription: Tunnel12 InterfaceBandwidth: 64 kbpsMaximum transmission unit: 1464Internet protocol processing: DisabledOutput queue - Urgent queuing: Size/Length/Discards 0/1024/0Output queue - Protocol queuing: Size/Length/Discards 0/500/0Output queue - FIFO queuing: Size/Length/Discards 0/75/0Last clearing of counters: NeverTunnel source 1.1.1.1, destination 2.2.2.2Tunnel protocol/transport UDP_VXLAN/IPLast 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/secLast 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/secInput: 5 packets, 300 bytes, 0 dropsOutput: 3 packets, 180 bytes, 0 dropsinterface Tunnel 13Tunnel13Current state: UPLine protocol state: UPDescription: Tunnel13 InterfaceBandwidth: 64 kbpsMaximum transmission unit: 1464Internet protocol processing: DisabledOutput queue - Urgent queuing: Size/Length/Discards 0/1024/0Output queue - Protocol queuing: Size/Length/Discards 0/500/0Output queue - FIFO queuing: Size/Length/Discards 0/75/0Last clearing of counters: NeverTunnel source 1.1.1.1, destination 3.3.3.3Tunnel protocol/transport UDP_VXLAN/IPLast 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/secLast 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/secInput: 16 packets, 960 bytes, 0 dropsOutput: 14 packets, 960 bytes, 0 drops
# 查看R1上的VSI虚接口信息,可以看到VSI虚接口处于up状态。
interface Vsi-interface 1Vsi-interface1Current state: UPLine protocol state: UPDescription: Vsi-interface1 InterfaceBandwidth: 1000000 kbpsMaximum transmission unit: 1500Internet address: 10.1.1.1/24 (Primary)IP packet frame type: Ethernet II, hardware address: 0001-0001-0001IPv6 packet frame type: Ethernet II, hardware address: 0001-0001-0001Physical: Unknown, baudrate: 1000000 kbpsLast clearing of counters: NeverLast 300 seconds input rate: 1 bytes/sec, 8 bits/sec, 0 packets/secLast 300 seconds output rate: 3 bytes/sec, 24 bits/sec, 0 packets/secInput: 9 packets, 570 bytes, 0 dropsOutput: 15 packets, 1020 bytes, 0 dropsinterface Vsi-interface 2Vsi-interface2Current state: UPLine protocol state: UPDescription: Vsi-interface2 InterfaceBandwidth: 1000000 kbpsMaximum transmission unit: 1500Internet address: 20.1.1.1/24 (Primary)IP packet frame type: Ethernet II, hardware address: 0002-0002-0002IPv6 packet frame type: Ethernet II, hardware address: 0002-0002-0002Physical: Unknown, baudrate: 1000000 kbpsLast clearing of counters: NeverLast 300 seconds input rate: 1 bytes/sec, 8 bits/sec, 0 packets/secLast 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/secInput: 9 packets, 570 bytes, 0 dropsOutput: 3 packets, 180 bytes, 0 drops
# 查看R1上的VSI信息,可以看到VSI内创建的VXLAN、与VXLAN关联的VXLAN隧道、与VSI关联的VSI虚接口等信息。
l2vpn vsi verboseVSI Name: vpnaVSI Index : 0VSI State : UpMTU : 1500Bandwidth : -Broadcast Restrain : -Multicast Restrain : -Unknown Unicast Restrain: -MAC Learning : EnabledMAC Table Limit : -MAC Learning rate : -Drop Unknown : -PW Redundancy : SlaveService Class : -Flooding : EnabledGateway Interface : VSI-interface 1VXLAN ID : 10Tunnels:Tunnel Name Link ID State Type Flood Proxy Split horizonTunnel12 0x500000c UP Manual Disabled EnabledTunnel13 0x500000d UP Manual Disabled EnabledACs:AC Link ID State0 UpVSI Name: vpnbVSI Index : 1VSI State : UpMTU : 1500Bandwidth : -Broadcast Restrain : -Multicast Restrain : -Unknown Unicast Restrain: -MAC Learning : EnabledMAC Table Limit : -MAC Learning rate : -Drop Unknown : -PW Redundancy : SlaveService Class : -Flooding : EnabledGateway Interface : VSI-interface 2VXLAN ID : 20Tunnels:Tunnel Name Link ID State Type Flood Proxy Split horizonTunnel12 0x500000c UP Manual Disabled EnabledTunnel13 0x500000d UP Manual Disabled EnabledACs:AC Link ID State0 Up
# 查看R1上VSI的ARP表项信息,可以看到已学习到了虚拟机的ARP信息。
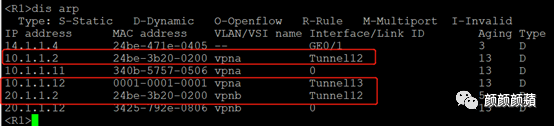
此时会发现R3设备下的10.1.1.12学习的 MAC地址为10.1.1.1网关的MAC。这就是在相同VXLAN内不同站点的虚拟机通信时,开启本地代理ARP后,所有流量都是三层转发,包括二层流量也需要查ARP表转发。当R3从VM 3收到ARP应答消息后,学习VM3的ARP信息,将ARP应答消息中的源MAC修改为本地VSI虚接口1的MAC地址,并根据已经学习到的ARP表项,为ARP应答消息添加VXLAN封装后发送给R1。R1对VXLAN报文进行解封装后,根据收到的ARP应答消息学习VM 3的ARP信息(IP为10.1.1.12、MAC为R3上VSI虚接口1的MAC、出接口为接收该VXLAN报文的Tunnel接口13)
(2)验证边界网关设备R2
# 查看R2上的Tunnel接口信息,可以看到VXLAN模式的Tunnel接口处于up状态。
interface Tunnel 21Tunnel21Current state: UPLine protocol state: UPDescription: Tunnel21 InterfaceBandwidth: 64 kbpsMaximum transmission unit: 1464Internet protocol processing: DisabledOutput queue - Urgent queuing: Size/Length/Discards 0/1024/0Output queue - Protocol queuing: Size/Length/Discards 0/500/0Output queue - FIFO queuing: Size/Length/Discards 0/75/0Last clearing of counters: NeverTunnel source 2.2.2.2, destination 1.1.1.1Tunnel protocol/transport UDP_VXLAN/IPLast 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/secLast 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/secInput: 3 packets, 180 bytes, 0 dropsOutput: 7 packets, 420 bytes, 0 dropsinterface Tunnel 23Tunnel23Current state: UPLine protocol state: UPDescription: Tunnel23 InterfaceBandwidth: 64 kbpsMaximum transmission unit: 1464Internet protocol processing: DisabledOutput queue - Urgent queuing: Size/Length/Discards 0/1024/0Output queue - Protocol queuing: Size/Length/Discards 0/500/0Output queue - FIFO queuing: Size/Length/Discards 0/75/0Last clearing of counters: NeverTunnel source 2.2.2.2, destination 3.3.3.3Tunnel protocol/transport UDP_VXLAN/IPLast 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/secLast 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/secInput: 11 packets, 660 bytes, 0 dropsOutput: 8 packets, 540 bytes, 0 drops
# 查看R2上的VSI虚接口信息,可以看到VSI虚接口处于up状态。
interface Vsi-interface 1Vsi-interface1Current state: UPLine protocol state: UPDescription: Vsi-interface1 InterfaceBandwidth: 1000000 kbpsMaximum transmission unit: 1500Internet address: 10.1.1.2/24 (Primary)IP packet frame type: Ethernet II, hardware address: 24be-3b20-0200IPv6 packet frame type: Ethernet II, hardware address: 24be-3b20-0200Physical: Unknown, baudrate: 1000000 kbpsLast clearing of counters: NeverLast 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/secLast 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/secInput: 11 packets, 660 bytes, 0 dropsOutput: 9 packets, 600 bytes, 0 dropsinterface Vsi-interface 2Vsi-interface2Current state: UPLine protocol state: UPDescription: Vsi-interface2 InterfaceBandwidth: 1000000 kbpsMaximum transmission unit: 1500Internet address: 20.1.1.2/24 (Primary)IP packet frame type: Ethernet II, hardware address: 24be-3b20-0200IPv6 packet frame type: Ethernet II, hardware address: 24be-3b20-0200Physical: Unknown, baudrate: 1000000 kbpsLast clearing of counters: NeverLast 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/secLast 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/secInput: 5 packets, 300 bytes, 0 dropsOutput: 2 packets, 120 bytes, 0 drops
# 查看R2上的VSI信息,可以看到VSI内创建的VXLAN、与VXLAN关联的VXLAN隧道、与VSI关联的VSI虚接口等信息。
l2vpn vsi verboseVSI Name: vpnaVSI Index : 0VSI State : UpMTU : 1500Bandwidth : -Broadcast Restrain : -Multicast Restrain : -Unknown Unicast Restrain: -MAC Learning : EnabledMAC Table Limit : -MAC Learning rate : -Drop Unknown : -PW Redundancy : SlaveService Class : -Flooding : EnabledGateway Interface : VSI-interface 1VXLAN ID : 10Tunnels:Tunnel Name Link ID State Type Flood Proxy Split horizonTunnel21 0x5000015 UP Manual Disabled EnabledTunnel23 0x5000017 UP Manual Disabled EnabledVSI Name: vpnbVSI Index : 1VSI State : UpMTU : 1500Bandwidth : -Broadcast Restrain : -Multicast Restrain : -Unknown Unicast Restrain: -MAC Learning : EnabledMAC Table Limit : -MAC Learning rate : -Drop Unknown : -PW Redundancy : SlaveService Class : -Flooding : EnabledGateway Interface : VSI-interface 2VXLAN ID : 20Tunnels:Tunnel Name Link ID State Type Flood Proxy Split horizonTunnel21 0x5000015 UP Manual Disabled EnabledTunnel23 0x5000017 UP Manual Disabled Enabled
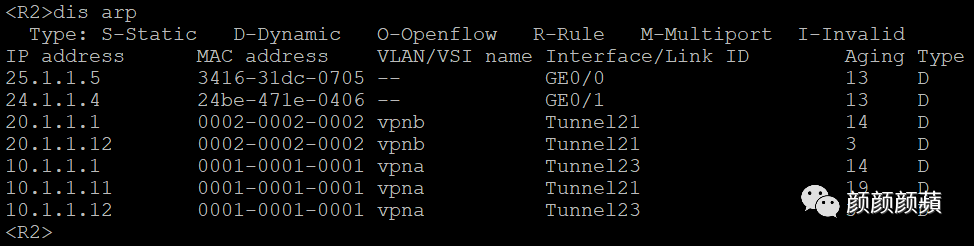
# 查看R2上VSI的ARP表项信息,可以看到已学习到了虚拟机的ARP信息。
(3)验证主机和广域网互访
从VM3(10.1.1.12)上测试:
<VM3>ping 10.1.1.11Ping 10.1.1.11 (10.1.1.11): 56 data bytes, press CTRL+C to break56 bytes from 10.1.1.11: icmp_seq=0 ttl=253 time=3.000 ms56 bytes from 10.1.1.11: icmp_seq=1 ttl=253 time=2.000 ms56 bytes from 10.1.1.11: icmp_seq=2 ttl=253 time=2.000 ms56 bytes from 10.1.1.11: icmp_seq=3 ttl=253 time=2.000 ms56 bytes from 10.1.1.11: icmp_seq=4 ttl=253 time=2.000 ms--- Ping statistics for 10.1.1.11 ---5 packet(s) transmitted, 5 packet(s) received, 0.0% packet lossround-trip min/avg/max/std-dev = 2.000/2.200/3.000/0.400 ms<VM3>%Aug 9 21:48:00:129 2021 VM3 PING/6/PING_STATISTICS: Ping statistics for 10.1.1.11: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 2.000/2.200/3.000/0.400 ms.<VM3>ping 20.1.1.12Ping 20.1.1.12 (20.1.1.12): 56 data bytes, press CTRL+C to break56 bytes from 20.1.1.12: icmp_seq=0 ttl=253 time=2.000 ms56 bytes from 20.1.1.12: icmp_seq=1 ttl=253 time=2.000 ms56 bytes from 20.1.1.12: icmp_seq=2 ttl=253 time=2.000 ms56 bytes from 20.1.1.12: icmp_seq=3 ttl=253 time=2.000 ms56 bytes from 20.1.1.12: icmp_seq=4 ttl=253 time=2.000 ms--- Ping statistics for 20.1.1.12 ---5 packet(s) transmitted, 5 packet(s) received, 0.0% packet lossround-trip min/avg/max/std-dev = 2.000/2.000/2.000/0.000 ms<VM3>%Aug 9 21:48:09:698 2021 VM3 PING/6/PING_STATISTICS: Ping statistics for 20.1.1.12: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 2.000/2.000/2.000/0.000 ms.<VM3>ping 25.1.1.5Ping 25.1.1.5 (25.1.1.5): 56 data bytes, press CTRL+C to break56 bytes from 25.1.1.5: icmp_seq=0 ttl=253 time=2.000 ms56 bytes from 25.1.1.5: icmp_seq=1 ttl=253 time=3.000 ms56 bytes from 25.1.1.5: icmp_seq=2 ttl=253 time=2.000 ms56 bytes from 25.1.1.5: icmp_seq=3 ttl=253 time=3.000 ms56 bytes from 25.1.1.5: icmp_seq=4 ttl=253 time=2.000 ms--- Ping statistics for 25.1.1.5 ---5 packet(s) transmitted, 5 packet(s) received, 0.0% packet lossround-trip min/avg/max/std-dev = 2.000/2.400/3.000/0.490 ms
查看ARP表项会发现由于开启本地代理,学习同网段地址MAC为网关MAC:
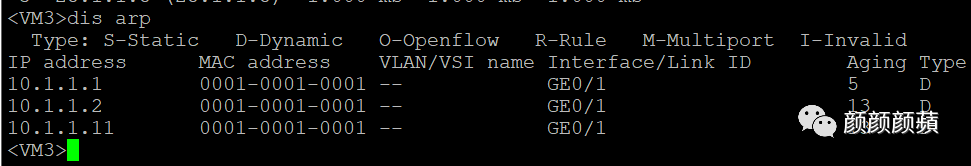
路由跟踪发现由于开启本地ARP代理,同网段访问时会经过两个分布式网关:
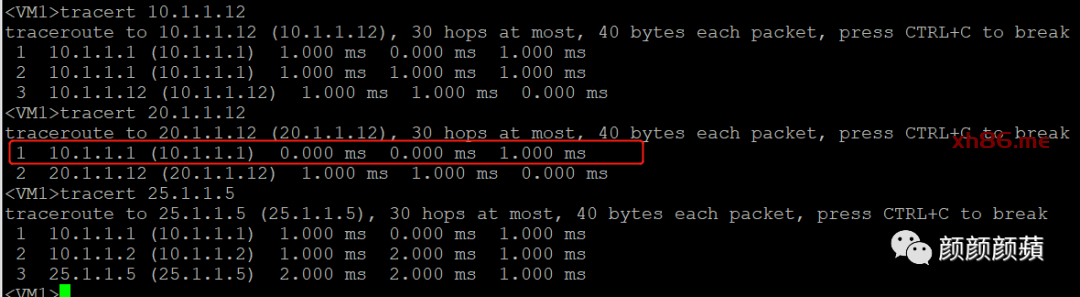
从VM1(10.1.1.11)上测试:
<VM1>ping 10.1.1.12Ping 10.1.1.12 (10.1.1.12): 56 data bytes, press CTRL+C to break56 bytes from 10.1.1.12: icmp_seq=0 ttl=253 time=3.000 ms56 bytes from 10.1.1.12: icmp_seq=1 ttl=253 time=2.000 ms56 bytes from 10.1.1.12: icmp_seq=2 ttl=253 time=2.000 ms56 bytes from 10.1.1.12: icmp_seq=3 ttl=253 time=2.000 ms56 bytes from 10.1.1.12: icmp_seq=4 ttl=253 time=2.000 ms--- Ping statistics for 10.1.1.12 ---5 packet(s) transmitted, 5 packet(s) received, 0.0% packet lossround-trip min/avg/max/std-dev = 2.000/2.200/3.000/0.400 ms<VM1>%Aug 9 21:55:39:147 2021 VM1 PING/6/PING_STATISTICS: Ping statistics for 10.1.1.12: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 2.000/2.200/3.000/0.400 ms.ping 20.1.1.12Ping 20.1.1.12 (20.1.1.12): 56 data bytes, press CTRL+C to break56 bytes from 20.1.1.12: icmp_seq=0 ttl=254 time=1.000 ms56 bytes from 20.1.1.12: icmp_seq=1 ttl=254 time=1.000 ms56 bytes from 20.1.1.12: icmp_seq=2 ttl=254 time=1.000 ms56 bytes from 20.1.1.12: icmp_seq=3 ttl=254 time=1.000 ms56 bytes from 20.1.1.12: icmp_seq=4 ttl=254 time=1.000 ms--- Ping statistics for 20.1.1.12 ---5 packet(s) transmitted, 5 packet(s) received, 0.0% packet lossround-trip min/avg/max/std-dev = 1.000/1.000/1.000/0.000 ms<VM1>%Aug 9 21:55:45:139 2021 VM1 PING/6/PING_STATISTICS: Ping statistics for 20.1.1.12: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 1.000/1.000/1.000/0.000 ms.<VM1>ping 25.1.1.5Ping 25.1.1.5 (25.1.1.5): 56 data bytes, press CTRL+C to break56 bytes from 25.1.1.5: icmp_seq=0 ttl=252 time=2.000 ms56 bytes from 25.1.1.5: icmp_seq=1 ttl=252 time=2.000 ms56 bytes from 25.1.1.5: icmp_seq=2 ttl=252 time=2.000 ms56 bytes from 25.1.1.5: icmp_seq=3 ttl=252 time=2.000 ms56 bytes from 25.1.1.5: icmp_seq=4 ttl=252 time=2.000 ms--- Ping statistics for 25.1.1.5 ---5 packet(s) transmitted, 5 packet(s) received, 0.0% packet lossround-trip min/avg/max/std-dev = 2.000/2.000/2.000/0.000 ms
VM1访问VM2由于是同一站点设备,所以只经过一跳设备:

VM2测试与VM1结果类似,此处不展示。
虚拟机VM 1、VM 2、VM 3之间可以互访;VM 1、VM 2和VM 3可以与R5上接口G0/0的地址25.1.1.5之间互访。
1.所有的分布式VXLAN IP网关(GW)上都需要创建VSI虚接口,并为不同GW上的相同VSI虚接口配置相同的IP地址,作为VXLAN内虚拟机的网关地址。否则在虚机迁移时网关的IP和MAC发生变化影响业务。
2.边界网关(Border)上也需要创建VSI虚接口,并配置IP地址。
3.在分布式VXLAN IP网关上还需要开启以下功能中的一种:
-
ARP泛洪抑制功能:开启本功能后,二层流量查找MAC地址表进行转发,三层流量查找ARP表项进行转发。
-
本地代理ARP功能或本地ND代理功能:开启本功能后,所有流量都通过查找ARP表项或ND表项进行三层转发。下文均以此功能为例,介绍分布式VXLAN IP网关中的通信过程。
4.如果虚拟机要想与外部网络进行三层通信,除以上配置外,还需要在接入虚拟机的本地分布式VXLAN IP网关上配置静态路由或策略路由:
-
配置静态路由:指定路由的下一跳为Border上同一个VXLAN对应VSI虚接口的IP地址。
-
配置策略路由:通过apply default-next-hop命令设置报文的缺省下一跳为Border上同一个VXLAN对应VSI虚接口的IP地址。
5.在分布式VXLAN IP网关设备上,如果开启了ARP泛洪抑制功能,并在VSI虚接口上开启了本地代理ARP功能,则只有本地代理ARP功能生效。建议不要在分布式VXLAN IP网关设备上同时开启这两个功能。